To learn more about users and their habits, companies need to dive deeper. One of the ways you can gain more insight is through user behavior analytics software. But can you easily understand this valuable tool? Can it provide actionable data? Yes! Here is a quick guide to help you get started.
There’s no denying that cybercrime is becoming a more serious issue for businesses in many countries, including the US and India. With the diversification of employment and work patterns in recent years, providing security with traditional security measures that only apply to specific sites and points has become more challenging. Users are becoming the security limits because even minor carelessness on humans, the users, might result in the disclosure of sensitive information. One of the best ways is to implement User Behavior Analytics tools (UBA) which are also called User and Entity Behavior Analytics (UEBA) that can help in fighting against cyber criminals.
According to the report from Dataprot stats, more than 68 records get stolen from the organization every second globally. In addition, it is found that the average data breach cost is around $3.92 million. Similarly, Verizon’s Data Breach Incident Report (DBIR) report states that insider assaults are perceived as a threat by 74% of businesses. There is a separate study conducted by the Carnegie Mellon University Software Engineering Institute, which states that insider attacks, compared to outside attacks are more damaging.
UBAs and UEBAs are technologies that can track activities on a network and alert users when they deviate from the norm. User behavior analytics tools can aid in detecting insider threats and preventing harmful attacks.
What are User Behavior Analytics and Tools?
User behavior analytics is integrated into employee monitoring and insider threat detection software. This tool collects data on each employee’s digital activities to learn more about how they work. The user behavior analytics definition by Gartner is user and entity behavior analytics provides complete profiling of the data based on various analytics approaches, which often combine fundamental analytics methods with advanced analytics. Vendors consider using analytics to help to understand the overall activities of users along with other entities. The process further helps to uncover potential incidents for users and entities.
UBA tools come with features having the potential to analyze historical data logs, stored in different forms in log management and SIEM systems. It further helps to discover traffic patterns coming from malicious user actions.
UBA carries more profiling and exception monitoring capabilities than the SIEM and is further utilized for two significant purposes. Firstly, UBA techniques are helpful to establish a baseline of routine activities that are unique to the company and its users. Secondly, these tools are beneficial to spot outliers or deviations from the norm, and UBA assesses these variances in near-real-time using big data and machine learning technologies.
A report from Accenture Security, “2017 Cost of Cyber-Crime Study,” presented that, on average, companies have to spend an annual cost of $11.7 million due to an increased cyber threat. All these have pushed the importance of user behavior analytics.
Not every time, do companies face employee time theft from outside but from the insiders. These insider threats are one of the major concerns for companies. Insider threat further results in a data breach, theft of intellectual property, and other organizational loss. This is where user behavior analytics enters the picture.
Different Types of Insider Threats
Current Employees– These employees unknowingly expose the system to a third party. It is the most common sort of insider threat. It occurs as a result of human error, such as leaving a gadget unattended or falling prey to a hoax.
Ex-employees– Someone who intentionally takes away the data from his/her current competitor employee to destroy the image and bring down the business.
Mole– An imposter gained insider access to a privileged network despite being nominally an outsider. This is someone who impersonates an employee or partner from outside the company.
Insider Threats are divided into three categories:
Compromised– The one who makes no conscious decision to act upon the data inappropriately.
Negligent– The same type of person does the act without any intention of harming the company
Malicious– If an employee appears disgruntled or has a grudge against someone, or if an employee begins to take on extra work with an unusual amount of zeal, this could be a sign of foul play.
Organizations can utilize employee time tracking software to get detailed data to understand typical user conduct, which can subsequently be used to spot odd or suspicious behavior.
How does UBA work?
Once you know the importance of user behavior analytics, you will also know that the tool is simply an algorithm that collects, analyses, and assesses the complete historical data, user activity, and security alerts.
It comprises individual user titles, access to given accounts, accounts and permissions, user activity, historical user infringement, and firewall detectors. Historical logs are utilize to collect and analyze data, but the system also keeps track of current activity, real-time resource usage, duration of sessions on accounts and within folders, connectivity, access points, and peer group activity.
The tool then compares the data’s interpretation to find probable “anomalous behavior”. When the system detects unusual behavior, it will automatically keep track of the activity.
How UBA Tools Identify Insider Threats?
Since the UBA software provides complete insight into insider risk intelligence, Cybersecurity teams may focus on decreasing the insider dangers to which they have been informed. The unit can also keep an eye on the UBA data in real-time to see if basic movement is happening beyond the point. An employee who has unauthorized access to a file or network can be detected by the cybersecurity team. It could also mean you have a careless insider, hacked credentials, or criminal behavior.
One of the essential features of UBA tools is that they don’t send too many false positives to the Cybersecurity team. The tool carries Machine Learning, Algorithms, and Statistics to construct and show a baseline behavior pattern or profile.
How do User Behavior Analytics Tools Help Organizations?
There are user behavior analytics examples or ways to present how they can help organizations. Some of them are-
- Detecting Potential Threat
No matter where a security breach occurs, it cannot always be avoided. Using user behavior analytics improves your chances of determining where the weaknesses are. If the breach was internal, you might be able to pinpoint the exact moment that a person inserted a USB drive or browsed a malware-infected website or document.
- Optimizing Business Processes
Organizations can use User Behavior Analytics Tools to undertake Business Process Mining. The data mining process involves evaluating what each person does in the organization, assessing the findings, and then devising a new approach based on the data.
How DeskTrack Worth Invest as a UBA Tool?
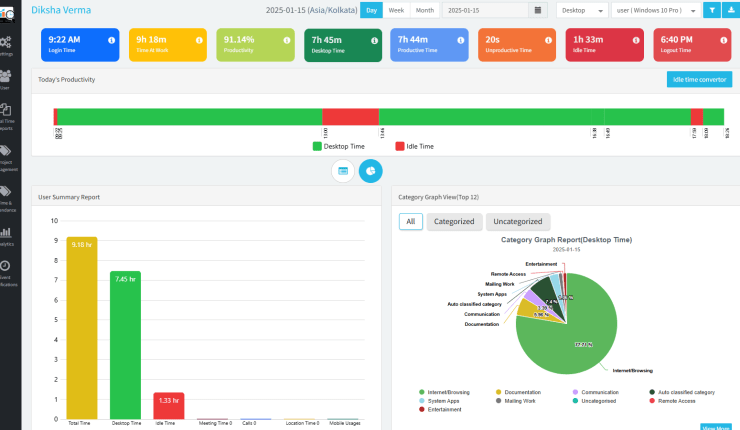
With DeskTrack, as a leading user behavior analytics software, an organization can also watch the unlawful activities done by the insider threat. If DeskTrack is configured to respond to unusual user behavior, DeskTrack will respond automatically. To safeguard your company’s network, use both reactive and proactive procedures. Some other ways DeskTrack User Behavior Analytics tool can assist:
- Filter through extensive activity and alert data quickly to find potentially dangerous actions.
- Notice any unexpected changes in the user’s schedule or idle time. Add context and intent to investigations using screenshots, videos, and other reports.
- The data is available on the screen within minutes of installation.
Pros and Cons
Here are the pros and cons of the tool:
Pros
- Complete Relevant Data- The tool offers relevant data that is useful for creating an anti-theft plan.
- Able to Predict Insider Threat- Has all the features to predict insider threat
- Easy to Install and use- As the time tracking software, the UBA is also easy to install and use.
Cons
Black Swan events or alert fatigue
UBA with machine learning can flag these activities as questionable when a user takes on a new job, works on a project that requires access to a new file or uses a new resource. These activities called ‘Black Swan’. Black Swan occurrences can cause ‘alert fatigue’ when you have so many alerts that you don’t know the most urgent or which ones to deal with first.
How to Choose the Best UBA Tools?
Once you understand the user behavior analytics definition and its importance, you can go ahead with purchasing this tool. However, there are other things, including-
- Are you concerned about too many data threats?
- Does insider threat worry you?
- Is any of the departments underperforming?
Conclusion
An insider cyber assault could happen to any firm, regardless of size or industry. Some businesses wait until they’ve had a data breach before putting security measures. Commit sure you don’t make this error. User Behavior Analytics provides security information personalized to your organization and prioritized by a security risk. Using DeskTrack User Behavior Analytics Software and an insider threat detection tool, you may proactively prevent data breaches.