In times when working remotely has become a very common culture. Not just a culture, instead a healthy practice wherein accessing talent has no bar & limits of commuting to the workplace. But also, it carries an obvious & likely probability of threat to the sensitive & confidential data of the organization. So, here we should begin to learn ways of implementing work from home software for data security.
4 Remote Work Security Challenges
No matter how secure technologies are provided to the employees working remotely, threats to data security are equally competent to nullify the same. Below are listed some common remote work security challenges to consider while allotting remote work to your employees:
1. Additional responsibility for data security is assigned to the employees – Employees are already occupied with their daily routine work. Assigning them with data security responsibility, without setting an appropriate policy in place would add an unnecessary task to their daily timetable.
2. Employees are unqualified to catch scams – Cyber scams are rarely explicit. During COVID-19, 4 out of 10 coronavirus-themed emails were proved to be spam, impersonating government & financial institutions. Therefore, employees are very vulnerable to overlook any such threat coming.
3. Employees use less secure Wi-Fi – Remote work has given this flexibility that employees can log in from anywhere. However, at the same time, employees are more vulnerable to cyberattack, when logging in from a public place. Though, employers nowadays have started using virtual private networks (as an extra layer of security), but such VPNs can be easily overloaded & overwhelmed too, as more people are working remotely than before.
4. Staff can overlook security priorities – During remote work, IT supervisors can easily lose sight of security measures & protocols. They may not have any clue whether security protocols are followed. Moreover, in the absence of such supervisors, employees too can take such security protocols for granted.
Make Your Workday More Productive
Time tracking and work management can help you reach your goals faster.
Try 15 Days for Free

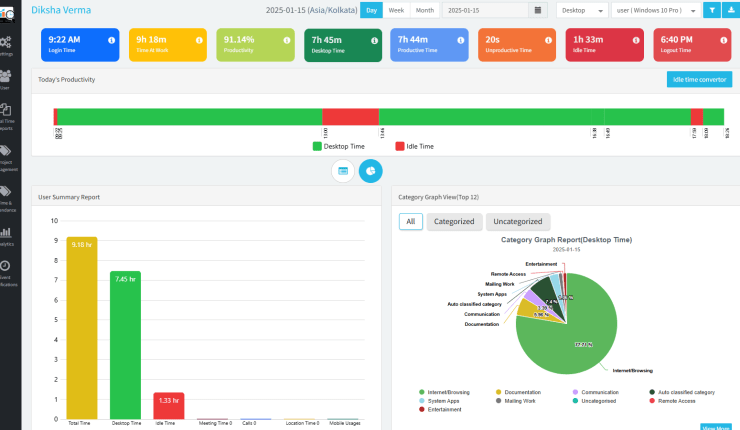
Ensure Data Security with DeskTrack
DeskTrack is all equipped for your organization’s data security & one of my personal choices as a work from home software. Its following features ensure the data & privacy protection:
Absolute Visibility
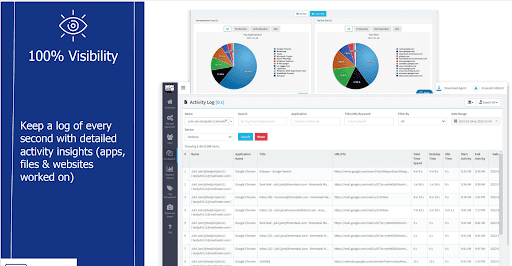
The work from home software ensures absolute visibility on every second activity performed on employees’ systems. It keeps a check on the apps, files & websites accessed by an employee.
Application Tracking
![]()
The work from home monitoring software ensures tracking of all the applications, URLs & websites, hence ensuring data leakage and unethical data sharing to a third party.
File Tracking
![]()
This feature of work from home software does file tracking for all types of offline files accessed by an employee. Again, this option of file tracking gives one more way of checking data breach.
Internet Usage
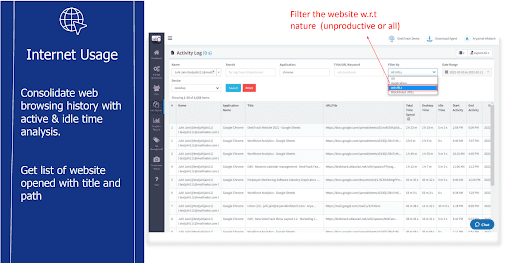
This feature provides a detailed path to the browsing history, along with a list of websites opened.
Real-time Screen View
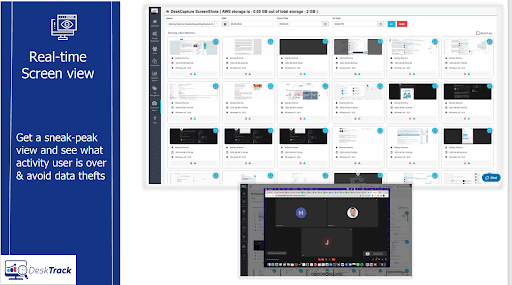
What can be better than keeping a real-time check? Screenshot monitoring software ensures the real-time screen view of systems. This system is appropriate for checking on any type of data theft.
Other Tips for Data Security in WFH
Here are some data security tips for for work from home employee:
Phishing Awareness
Your organization should spread phishing awareness amongst WFH employees. Typically, it’s a part of a cybersecurity training program. Besides, ensure to stay updated about the latest phishing scams, thereby communicating the relevant guidelines & warnings to the employees.
Additionally, for employees, here are some important tips to avoid phishing awareness:
- Avoid email, SMS, or social media messages unless you verify the sender.
- Do not download email links or attachments, received from an unknown sender.
- While visiting a website, check for a ‘padlock’ symbol in your browser address bar.
Allot Company Approved Devices
Plan for an appropriate ‘remote-work setup’. Ideally, your employees should be able to access company data under the company’s control.
It’s not that tough to implement! You can simply ask for the device’s specifications on which an employee is doing his daily company operations.
Secure Company Devices
Needless to say, your IT team must frame certain policies to secure employees’ devices. One such policy is ‘locking device’ when not in use. The team can set minimum standards for device-locking, for instance:
- Minimum length of password
- Unlock methods (pattern, PIN, fingerprint)
- Fixed timeout period (after which the device gets locked automatically)
- Implement multi-factor verification
Use Work Email Accounts
Check that your employees do not forward work-related emails to their email ids. It risks confidentiality. The IT team should make it clear that the remote working employees should only use company email accounts for correspondence.
Putting it in a Nutshell!
To suggest the best, choose a work from home software that not only checks the productivity delivered by the employees but also checks for data security & data thefts. To my personal experience, DeskTrack has been performing the best till now, as a remote employee monitoring software.
Not only this, the work from home software has always been upgraded to the best version which supports the requirement of nowadays data security.